Imagine your personal data as precious jewels stored in a vault. In the digital world, privacy engineering is comparable to the design and construction of that vault. It’s about creating secure, robust, and user-friendly environments that protect these jewels from thieves and unauthorized access. As our lives become increasingly digital, the need to safeguard personal information has never been more critical. This article delves into the intricacies of privacy engineering, exploring its principles, challenges, and the impact of regulatory frameworks like the Digital Personal Data Protection (DPDP) Act.
1. What is Privacy Engineering?
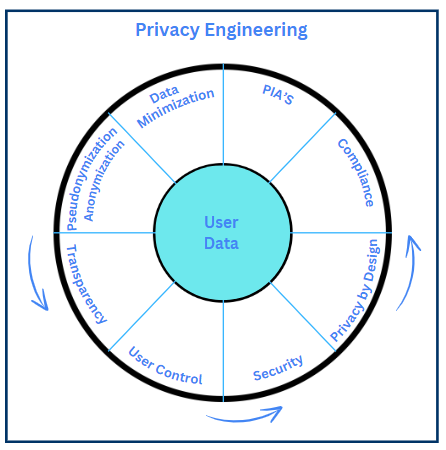
Privacy engineering refers to the application of engineering principles to build systems and processes that safeguard user privacy. It encompasses methodologies, tools, and technologies required to design and implement data protection measures across various digital platforms. Privacy engineering aims to ensure that privacy is not an afterthought but a core component of the system from the outset.
1.1 Why was there a need for Privacy Engineering?
The need for privacy engineering has evolved with the rise of digital technologies. Early concerns were focused on physical documents, but the advent of the internet and digital storage brought new challenges. Notable privacy breaches, such as the Facebook-Cambridge Analytica scandal, have underscored the importance of robust privacy measures. These incidents have catalysed the development of privacy engineering as a field, highlighting the need for proactive and preventive measures to protect personal data.
2. Core Principles of Privacy Engineering
2.1 Data Minimization:
Collecting only the data necessary for the intended purpose is a cornerstone of privacy engineering. Data minimization involves assessing what data is truly needed and ensuring that unnecessary data is not collected or retained, thus reducing the risk of data breaches and limiting the impact if a breach occurs.
Alignment with DPDP Act: The DPDP Act emphasizes data minimization by mandating that data fiduciaries (entities that process personal data) should only collect data that is necessary for specified purposes. This aligns with the principle of minimizing data to protect user privacy, ensuring that organizations do not collect or hold excessive data that could increase the risk of misuse or breaches.
2.2 Anonymization and Pseudonymization:
These are critical techniques in privacy engineering. Anonymization involves removing or altering personal identifiers so that data cannot be traced back to an individual, while pseudonymization replaces private identifiers with fake ones. Both techniques help protect personal identities while still allowing data to be used for analysis.
Alignment with DPDP Act: The DPDP Act encourages anonymization and pseudonymization as key strategies to safeguard personal data, making it harder for unauthorized entities to link data back to individuals. This ensures a higher level of data protection while maintaining the utility of the data for analysis and insights.
2.3 Transparency:
Being open and clear with users about data collection and usage practices is vital. Transparency involves clearly communicating what data is collected, how it is used, and who it is shared with. Effective transparency can be achieved through well-designed privacy policies and user interfaces that provide this information in an understandable and accessible manner.
Alignment with DPDP Act: The DPDP Act mandates transparency by requiring data fiduciaries to inform individuals about data collection and processing activities. This ensures that users are aware of how their data is handled and can make informed decisions, aligning with the principle of providing clear and accessible information to data subjects.
2.4 User Control:
Empowering individuals to manage their privacy by providing mechanisms for them to access, modify, or delete their data is essential. Consent management systems and preference settings are tools that give users control over their personal data.
Alignment with DPDP Act: The DPDP Act grants individuals the right to access, correct, and erase their personal data, reinforcing the principle of user control. This empowerment of users to manage their privacy effectively ensures that they have a say in how their data is used and protected.
2.5 Security Measures:
Implementing robust security measures to protect personal data is integral. This includes encryption, access controls, and regular security audits to prevent unauthorized access and data breaches. These measures should be continuously updated to address evolving threats.
Alignment with DPDP Act: The DPDP Act requires data fiduciaries to implement appropriate security measures to protect personal data from breaches. This aligns with the principle of ensuring strong data security, making it mandatory for organizations to continuously enhance their security protocols to safeguard personal information.
2.5 Privacy by Design and Default
Privacy by Design involves embedding privacy into the design of systems and processes from the outset. Privacy by Default ensures that privacy settings are automatically configured to the highest level of protection.
Implementation Strategies: To integrate these principles, organizations should conduct privacy impact assessments during the development phase and continuously monitor and update privacy practices. This proactive approach ensures that privacy considerations are not overlooked.
Alignment with DPDP Act: The DPDP Act emphasizes the importance of incorporating privacy by design and default, encouraging organizations to proactively embed privacy into their systems and operations. This alignment ensures that privacy is not just an afterthought but a fundamental aspect of the system architecture.
2.6 Regulatory Compliance
Key privacy regulations like the GDPR, CCPA, and HIPAA have set standards for data protection globally. The DPDP Act is India’s response to the growing need for robust data protection frameworks.
Compliance Strategies: Organizations must understand the requirements of these regulations and implement necessary measures, such as conducting privacy impact assessments and appointing data protection officers.
Alignment with DPDP Act: The DPDP Act outlines specific obligations for data fiduciaries, including obtaining consent, ensuring data security, and providing mechanisms for data subject rights, aligning with global privacy standards. This ensures that organizations adhere to strict data protection measures, maintaining compliance and protecting user data.
Table mapping the Digital Personal Data Protection (DPDP) Act with key principles of privacy engineering:
| DPDP Act Requirement | Privacy Engineering Principle |
|---|---|
| Data Minimization | Collect only necessary data for specified purposes to minimize risks. |
| Anonymization and Pseudonymization | Implement techniques to protect personal identities while using data for analysis. |
| Transparency | Ensure clear communication with users about data collection and usage practices. |
| User Control | Empower users with rights to access, modify, or delete their personal data. |
| Security Measures | Implement robust security measures like encryption and access controls to prevent unauthorized access to data. |
| Privacy by Design and Default | Embed privacy into system design and ensure that privacy settings are configured to the highest level of protection. |
| Compliance with Global Privacy Standards | Align with international standards (e.g., GDPR, CCPA) and local regulations (DPDP Act) to ensure data protection. |
| Privacy Impact Assessments and Monitoring | Conduct privacy impact assessments and continuously monitor privacy practices to maintain compliance and effectiveness. |
Securing User Data: Aligning with the DPDP Act and Privacy Engineering
3. Challenges in Privacy Engineering
3.1 Technical Complexity: Integrating robust privacy measures like encryption and access controls into complex systems without compromising functionality or scalability.
3.2 Regulatory Compliance Burden: Adapting to evolving privacy laws such as GDPR, CCPA, and DPDP Act requires continuous monitoring and adjustment of privacy practices across different jurisdictions.
3.3 Data Security Risks: Mitigating cybersecurity threats and ensuring data protection through measures like encryption and access controls to prevent breaches and unauthorized access.
3.4 User Expectations versus Regulatory Requirements: Balancing user expectations for personalized services with stringent regulatory mandates for consent and transparent data handling practices.
3.5 Organizational Culture and Awareness: Establishing a privacy-aware culture from top management to frontline staff through clear policies, regular training, and embedding privacy into corporate values and practices.